Protecting WordPress Files With Amazon S3
If you’re storing private files in WordPress and hoping your shared hosting setup will magically keep them safe… that’s a bold strategy.
In reality, if you sell digital products, host member-only content, or store any kind of sensitive media, you’ll eventually hit the limits of WordPress’ default file handling. That’s where Amazon S3 + proper file protection comes in.
Let’s walk through how to use Amazon S3 for WordPress file protection in a way that’s secure, scalable, and not a total pain to manage.
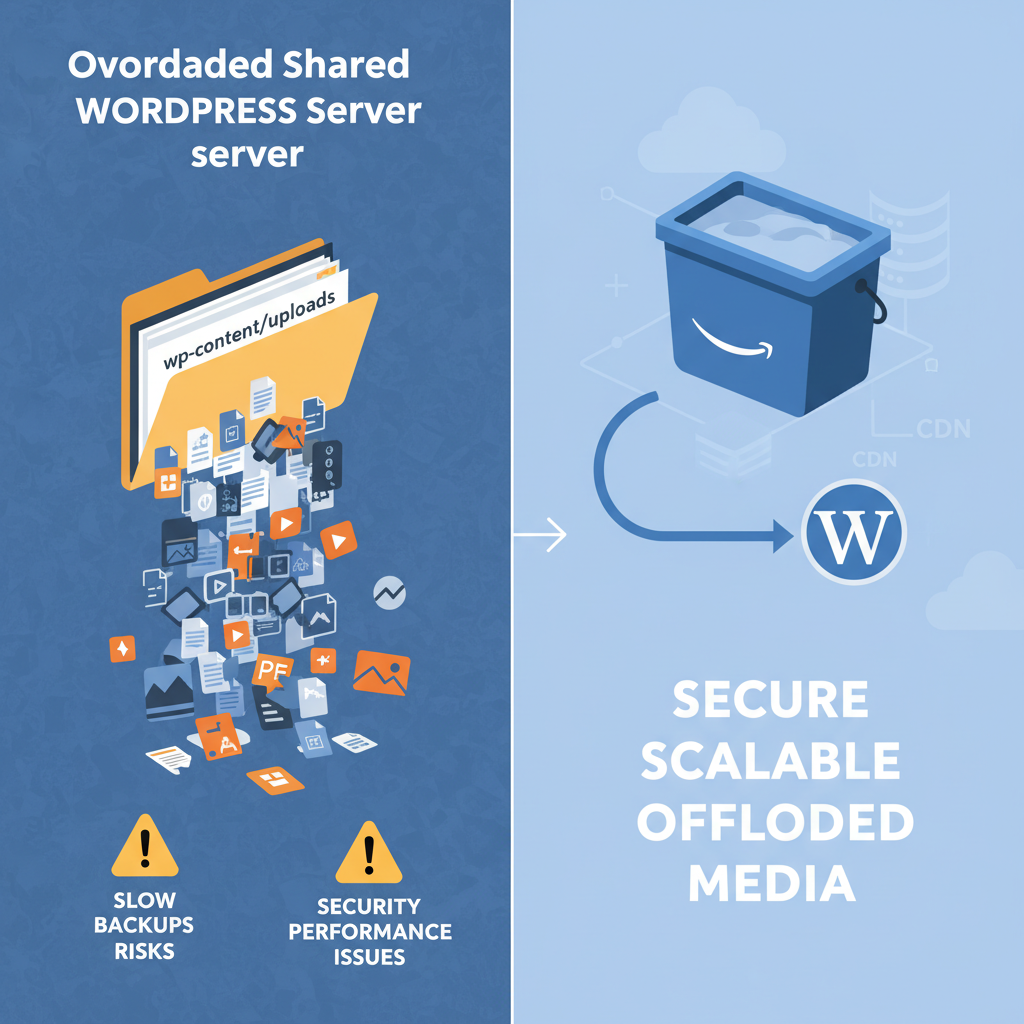
Offloading heavy, sensitive media from your shared WordPress hosting to S3 is the difference between “it kind of works” and “this will scale without melting.”
Why move WordPress files to Amazon S3 at all?
Before we talk protection, let’s talk why.
Most WordPress sites start by dumping everything into /wp-content/uploads/. It works… until it doesn’t:
- Anyone who knows (or guesses) the URL can access public files directly.
- Backups get huge and slow because they include gigabytes of media.
- Shared hosting chokes when you start serving big files or lots of downloads.
Amazon S3 (Simple Storage Service) solves a bunch of this in one move:
- Designed for massive, cheap, reliable file storage.
- Plays nicely with CDNs (like Amazon CloudFront) so downloads are fast globally.
- Supports fine-grained access control, temporary links, and logs.
Key takeaway: WordPress is great at content management. S3 is great at file storage and access control. Combining them gives you both power and safety.
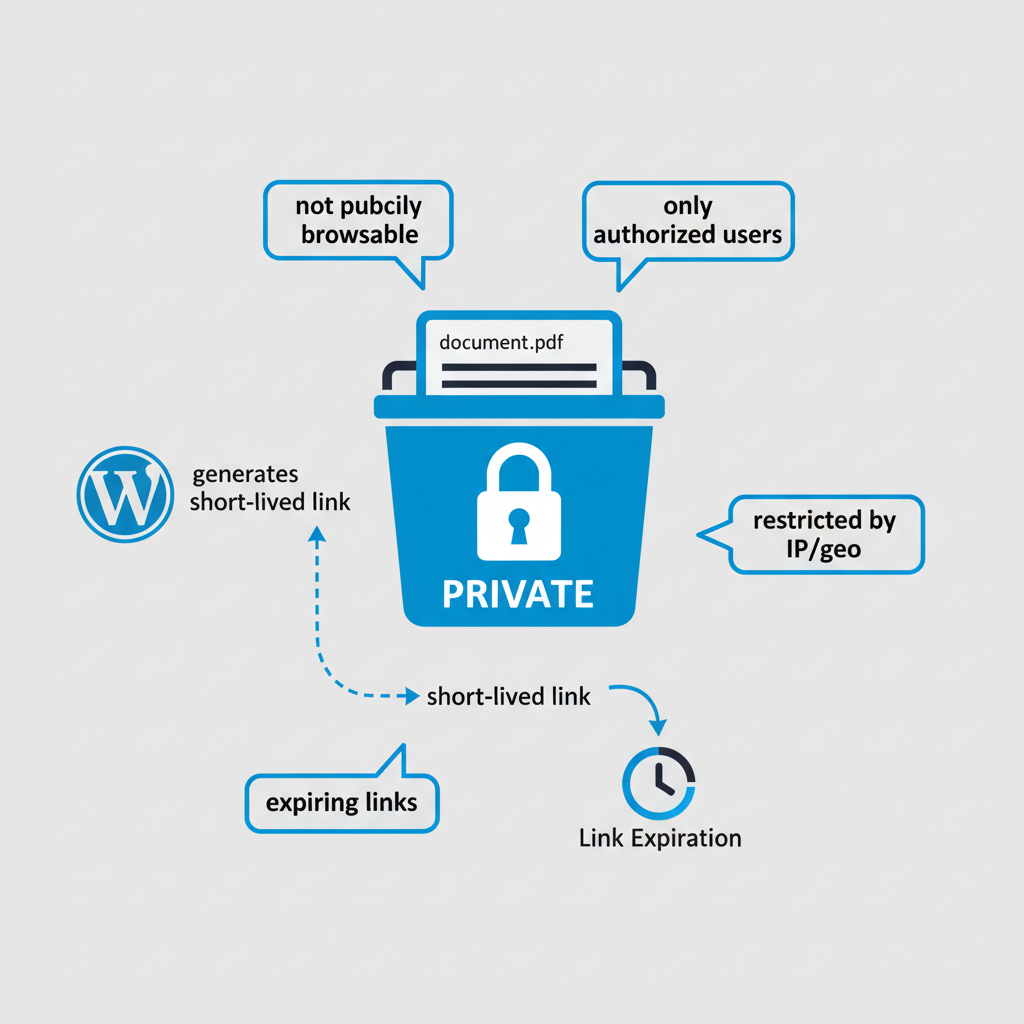
Think of S3 as your locked vault; WordPress just hands out temporary visitor badges to the right people.
What does “file protection” on S3 actually mean?
When people say “protect my files on S3,” they usually mean at least one of these:
- Files are not publicly browsable — you can’t just hit a URL and see everything.
- Only logged-in or paying users can access specific files.
- Links expire after a short time, so they can’t be shared freely.
- Traffic can be restricted by domain, IP, geography, or signed cookies/URLs.
On Amazon S3 + WordPress, that typically translates to:
- Private S3 buckets or private objects (nothing public by default).
- Presigned URLs or signed CloudFront URLs generated on the fly.
- WordPress-level access rules (memberships, roles, LMS rules, etc.) that decide who gets a link.
Key takeaway: Protecting files isn’t just “hide the URL.” It’s controlling who can get a time-limited way to download or view them.
Once you understand buckets, objects, policies, and IAM, the rest of the S3 + WordPress puzzle snaps into place.
Core concepts you need to know (S3 + WordPress)
You don’t need to be a full-on AWS engineer, but a few concepts will save you hours:
1. S3 Buckets & Objects
- A bucket is like a top-level folder (e.g.,
mycourse-files). - An object is a file in that bucket (e.g.,
module-1/video.mp4).
You’ll typically create one or a few buckets per project and organize by folder paths.
2. Bucket Policies & Object ACLs
You can control access in two main ways:
- Bucket policy: rules that apply to all objects in the bucket (preferred).
- Object ACLs: permissions per file (use sparingly; easier to mess up).
For private WordPress files, you usually:
- Set the entire bucket to block public access.
- Keep objects private.
- Let your application (WordPress) access S3 via IAM credentials.
3. IAM Users & Roles
AWS IAM controls who or what can talk to S3.
For a WordPress site, you usually:
- Create an IAM user with programmatic access only.
- Give that user restricted S3 permissions to just the bucket(s) it needs.
- Use those keys in your WordPress plugin or config.
Key takeaway: Lock the bucket down, and let only your WordPress app talk to it with properly scoped IAM permissions.
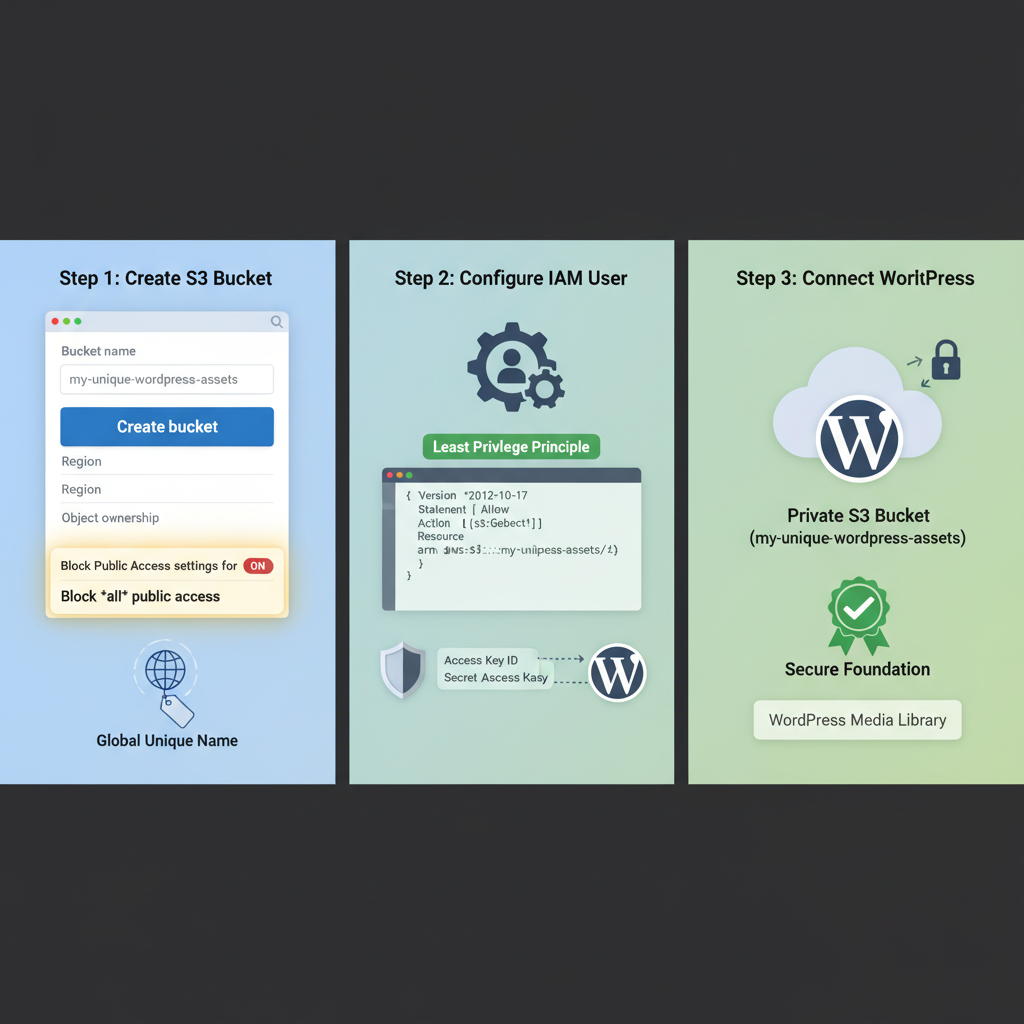
Dial in the foundation once and every protected download your site serves rides on top of it.
Step-by-step: Setting up a private S3 bucket for WordPress
Let’s build the secure foundation before we wire it into WordPress.
Step 1: Create a private S3 bucket
- Log in to your AWS console and go to S3.
- Click Create bucket.
- Choose a globally unique name (e.g.,
mybrand-protected-files). - Pick a region close to your main audience.
- Uncheck any option that makes objects public by default.
- Under Block Public Access, keep everything ON (block all public access).
Result: You now have a bucket that’s not accessible to the public Internet.
Step 2: Set up IAM credentials with least privilege
- Go to IAM in AWS.
- Create a new IAM user (e.g.,
wp-s3-file-access). - Enable Programmatic access.
- Attach a policy that:
- Allows listing and reading objects only in your bucket.
- Optionally allows writing (if you want WordPress to upload directly to S3).
A minimal JSON policy (you’d customize bucket name and actions):
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::mybrand-protected-files"
]
},
{
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:PutObject"
],
"Resource": [
"arn:aws:s3:::mybrand-protected-files/*"
]
}
]
}Save the Access key ID and Secret access key — you’ll need them in WordPress.
Step 3: Decide how WordPress will talk to S3
There are two common options:
- Use a mature plugin to integrate S3 and protect files.
- Roll your own code (or custom plugin) for maximum control.
If you’re not a developer or don’t have one on call, use option 1.
Typical use cases + plugin types:
- Offload all media (public + protected): S3 offload plugins that replace
/wp-content/uploads/with S3 URLs. - Protect specific download files: Membership/LMS/download manager plugins with S3 integration.
Key takeaway: S3 is the storage; WordPress plugins become the brains that decide who gets access.
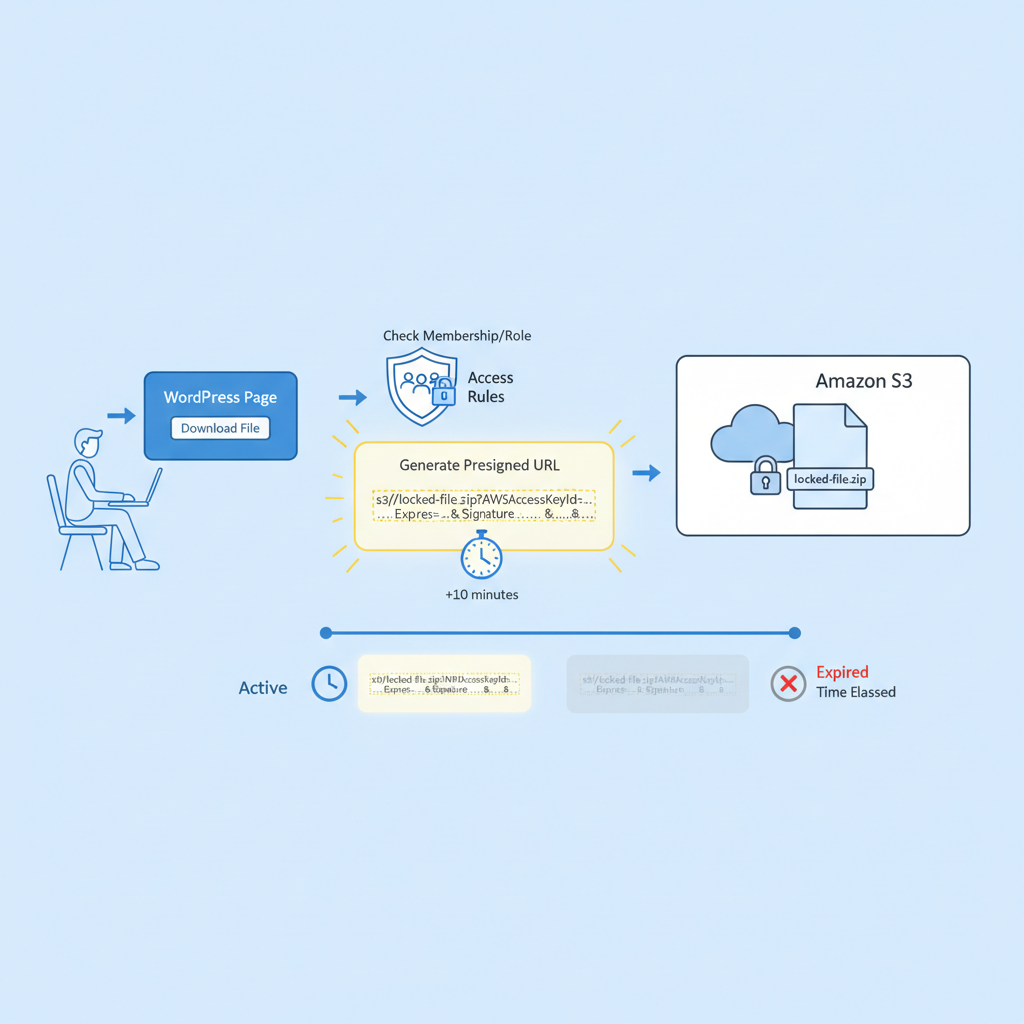
Under the hood, every “Download” button on your site can quietly run an access check and hand out a temporary, one-off key.
How to protect files using presigned URLs
A presigned URL is a temporary, access-granted link to a private S3 object. It says:
“For the next X minutes, this otherwise private file can be downloaded using this URL. After that, nope.”
This is the core of secure downloads with Amazon S3 and WordPress.
How presigned URLs usually work with WordPress
- A user tries to download a file (e.g.,
mycourse.com/download/module-1). - WordPress checks: is this user allowed?
- Logged in?
- Has the right membership, role, or purchase?
- If no, show an error or redirect.
- If yes, your plugin or custom code uses the AWS SDK to:
- Generate a presigned URL to the S3 object.
- Set a short expiration (e.g., 2–10 minutes).
- WordPress redirects the user to that presigned URL.
So even if they copy the link and send it to a friend an hour later, it no longer works.
Example: Generating a presigned URL in PHP
If you’re rolling custom code (simplified example):
use Aws\S3\S3Client;
use Aws\S3\Exception\S3Exception;
$s3 = new S3Client([
'version' => 'latest',
'region' => 'us-east-1',
'credentials' => [
'key' => 'AWS_ACCESS_KEY_ID',
'secret' => 'AWS_SECRET_ACCESS_KEY',
],
]);
$cmd = $s3->getCommand('GetObject', [
'Bucket' => 'mybrand-protected-files',
'Key' => 'course/module-1/video.mp4',
]);
$request = $s3->createPresignedRequest($cmd, '+10 minutes');
$presignedUrl = (string) $request->getUri();You would then redirect the authorized user to $presignedUrl.
Key takeaway: Presigned URLs are your best friend for S3 file protection — secure, temporary, and fully controlled in WordPress.
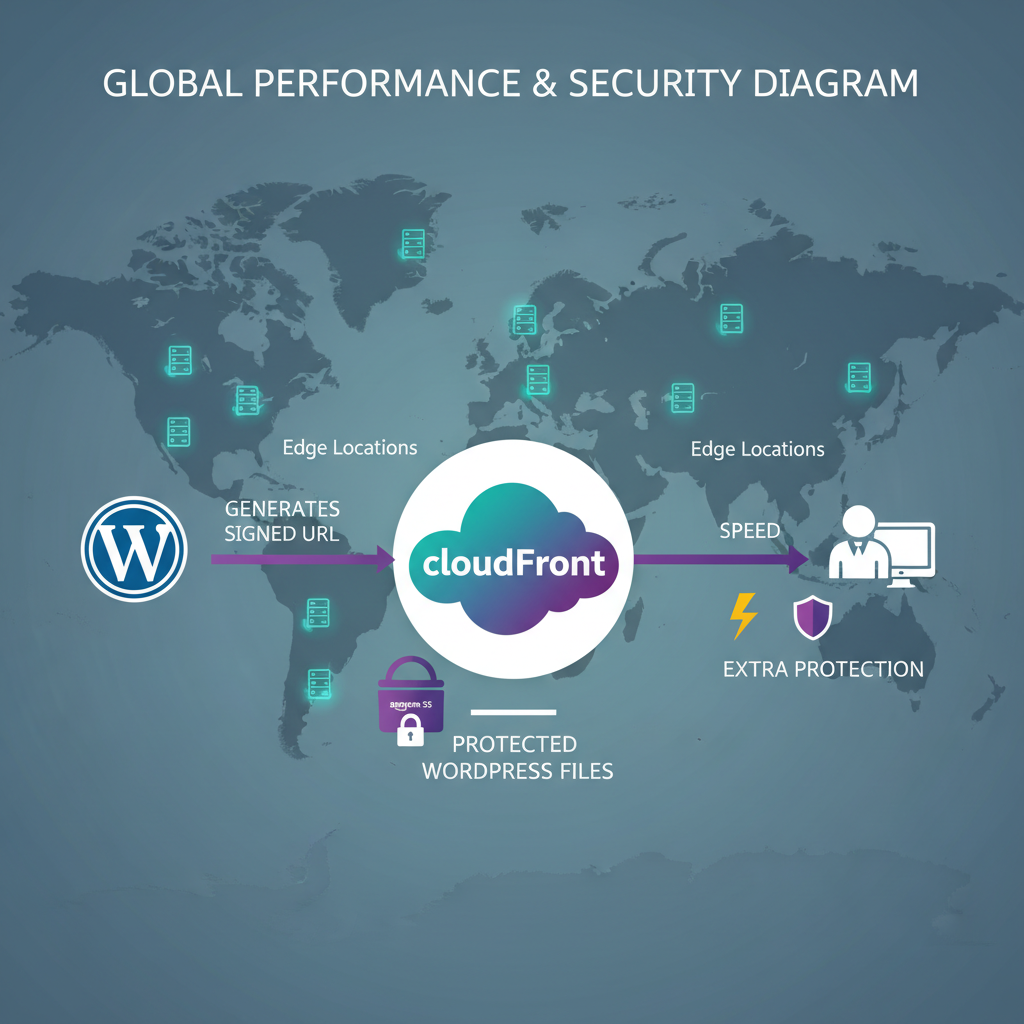
Add CloudFront in front of S3 and your protected content goes from “secure” to “secure and fast everywhere.”
Adding CloudFront for speed and extra protection
If your files are large (videos, big PDFs, zips) or your users are global, you’ll want Amazon CloudFront — AWS’s CDN.
CloudFront can:
- Cache your S3 files closer to users for faster downloads.
- Require signed URLs or signed cookies, adding another layer beyond S3.
- Let you restrict access by referer, geo, or IP.
Common setup pattern
- Create a CloudFront distribution with your S3 bucket as the origin.
- Configure it to use an Origin Access Control/Identity (OAC/OAI) so CloudFront can access S3, but the public cannot.
- Lock your S3 bucket policy so only CloudFront can read from it.
- Use signed CloudFront URLs from WordPress instead of raw S3 presigned URLs.
You can still keep the same flow:
- User requests file → WordPress checks permissions → WordPress generates signed CloudFront URL → User downloads via CDN.
Key takeaway: CloudFront makes your protected S3 files fast and adds another gate in front of S3.
Real-world scenarios: How you’d actually use this
Scenario 1: Protecting digital product downloads in WooCommerce
You sell ebooks, templates, or software.
- Store all downloadable files in a private S3 bucket.
- Use a WooCommerce-compatible S3/download protection plugin.
- After purchase, customers see a protected download link.
- The plugin generates a presigned URL for each request, with:
- Limited number of downloads.
- Short URL expiry.
Result: Customers can download without hassle, but your files aren’t sitting in /wp-content/uploads/ for anyone to grab.
Scenario 2: Membership site with premium content
You run a membership site or course platform on WordPress.
- Videos, PDFs, and worksheets live in a private S3 bucket.
- Membership plugin (or LMS) integrates with S3.
- Only logged-in members with the right level can access certain content.
- On access, the plugin creates a short-lived S3 or CloudFront URL.
Result: Cancelled member? Access gone. Shared link? Expired. Still friendly to legitimate users.
Scenario 3: Internal files or client deliverables
You run an agency or internal portal where clients/employees download reports.
- Private S3 bucket with separate folders per client or department.
- WordPress controls which user role can see which folder.
- Each download uses a presigned URL.
Result: Cleaner permissions and no more “Can you email me that again?” chaos.
Common mistakes (and how to avoid them)
Even smart teams trip on these:
1. Leaving the bucket (or some objects) public
If anything is public in a bucket you think is private, assume users will find it.
Fix:
- Turn on Block Public Access at the bucket level.
- Avoid public ACLs on individual objects.
2. Over-permissive IAM policies
Granting s3:* on * looks tempting when you’re debugging, but it’s a future security incident.
Fix:
- Limit IAM policies to only the bucket(s) and actions your site truly needs.
- Use separate IAM users/roles for staging vs production if possible.
3. Presigned URLs that never expire
If you set very long expirations (days/weeks), people will share them around.
Fix:
- Use short lifetimes (5–15 minutes) for most use cases.
- For large downloads, pair shorter URL lifetimes with download managers or resume support.
4. Mixing public and private access without a plan
If you serve some assets publicly (images) and some privately (downloads), you can end up confused about which is which.
Fix:
- Use separate buckets for public vs protected content, or at least clear folder structures like
/public/vs/protected/. - Document your structure for your team.
Key takeaway: A little discipline in IAM, bucket settings, and URL expirations goes a long way.
Quick checklist: Secure Amazon S3 WordPress file protection
Use this as your sanity check:
- S3 bucket created with Block Public Access enabled
- Objects are not publicly readable
- IAM user/role has minimal privileges to that bucket
- WordPress is using a stable plugin or custom code to integrate S3
- Access to files is tied to user login / membership / purchase
- Presigned URLs or signed CloudFront URLs are used for downloads
- URL expiration is kept short (minutes, not days)
- (Optional) CloudFront distribution sits in front of S3 for speed and extra control
If you can check all of these, your protected files are in a much safer place than the default /wp-content/uploads/ free-for-all.
Where to go from here
If you’re starting from a typical WordPress install with everything in local storage, your first move is simple:
- Create a private S3 bucket.
- Pick a WordPress plugin that supports S3 + protected downloads.
- Migrate just one type of asset first (for example, paid downloads), not everything at once.
Once that’s stable, you can:
- Add CloudFront for speed.
- Gradually offload large media.
- Tighten IAM and logging.
Do it step by step and test each piece. Your future self (and your paying customers) will be very grateful that those files aren’t just sitting on a public URL anymore.